ICT338 Information Security Challenges in Smart Computing Assignment, SUSS, Singapore: Samuel the system administrator has discovered malicious remote connection(s) activities while performing a routine check
Question 1
Samuel the system administrator has discovered malicious remote connection(s) activities while performing a routine check on his company web server’s log. He had retrieved a Wireshark capture of the malicious network activities for further investigation. Apply the use of Wireshark and assess the given network traffic ICT338 2023 ECA Q1.pcap and answer all the questions below. Explanation and screenshots of the evidence from the Wireshark application must be provided together with the answers.
i. What is the web server’s IP address?
ii. What is the attacker’s IP address?
iii. What technique is the attacker using to gain remote access to the victim’s server? Provide the transport layer protocol and port number used by the attacker for the malicious connection.
iv. What operating system and version is running on the web server?
v. What is the name of the malicious script used by the attacker?
Hire a Professional Essay & Assignment Writer for completing your Academic Assessments
Question 2
You are working on an IoT pilot project that involves collecting temperature and humidity data from a network of temperature and humidity sensors. There are three types of sensors. Temperature sensor type T-U1, temperature type T-E2, and humidity sensor type H-S1. Temperature sensor type T-U1 measures temperature to the nearest ºF, temperature sensor type T-E2 measures temperature to the nearest 0.1 ºC, and humidity sensor H-S1 measures humidity levels to the nearest %. Each sensor sends a message to a central server in the format shown in the following.
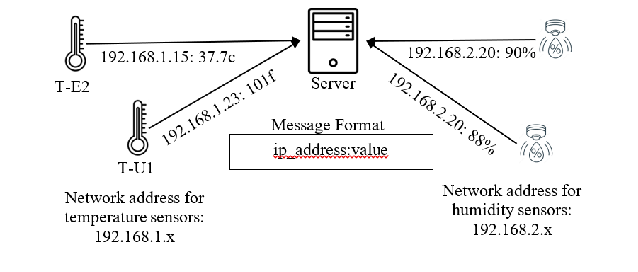
Question 2a
Write a regular expression that can be used to determine the validity of received messages.
Question 2b
Demonstrate the effectiveness of the proposed regular expression using
www.regex101.com or any other regular expression testing tools using appropriate test data. Include screenshots of your testing and provide an explanation of the test results.
Question 2c
6 months after the project, it was reported that environmental data was stolen from the network while it was being transmitted from the sensors to the server. The management has decided that encryption of data-in-motion should be implemented. Recommend an encryption type (symmetric or asymmetric) and assess the merits of your recommendation.
Buy Custom Answer of This Assessment & Raise Your Grades
Question 3
A ride-sharing company called Ubber is planning to launch a smart ride-sharing application with an initial user base of 50,000 in Singapore. The eventual goal is to expand this application to the rest of Southeast Asia spanning 10 countries with a targeted user base of 50 million users.
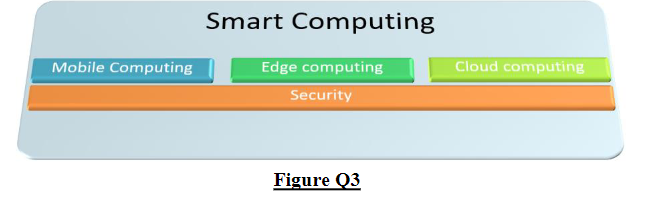
Question 3a
With reference to Figure Q3, appraise the key capabilities required and explain why these capabilities are required for the success of the ride-sharing application.
Stuck with a lot of homework assignments and feeling stressed ? Take professional academic assistance & Get 100% Plagiarism free papers
Singapore students pursuing their studies at the Singapore University of Social Science (SUSS) can now access expert help for their academic assignments and coursework. Whether it's tackling a challenging ICT338: Information Security Challenges in Smart Computing Assignment or seeking assistance with TMA (Tutor Marked Assignments), our specialized Assignment Help Singapore service is here to support you. Our dedicated team of professionals offers top-notch Essay Writing Services tailored to your needs. Say goodbye to academic stress and let our experts assist you in achieving academic success.
- COU104e Social and Emotional Learning TMA: Competencies, Community Impact & Stress Management
- HBC251 Religion in Contemporary Societies TMA02: Site Visit & Interfaith Analysis
- BSL202 Workplace Law Assignment: Employment Status and Contractual Obligations
- HRM335 Leadership Development TMA01: A Personal Leadership Metaphor and Action Plan
- BUS100 Business Skills and Management TMA: E-Commerce and Financial Analysis
- PSY205 ECA Guidelines: Integrated Public Safety and Security Management
- PSY205 Social Psychology TMA02: Submission Guidelines and Requirements
- Math255 Mathematics for Computing Assignment: Statistical Methods and Probability
- SWK352 TMA: Assessing Sharon’s Challenges in Child Development
- COS364 Tutor-Marked Assignment: Working with Interventions for At-Risk Youths
UP TO 15 % DISCOUNT

