CSCI368 Network Security Assignment, UOW, Singapore: Consider the following key exchange protocol which is a variant of the Diffie-Hellman protocol
| University | University of Wollongong (UOW) |
1. Consider the following key exchange protocol which is a variant of the Diffie-Hellman protocol. Each user P has a secret key sk_P=x_P and public key pk= gx_P mod p.
1: A B: gr_A mod p
2: B A: gr_B mod p
In the protocol, r_A and r_B are randomly chosen in each session by A and B. The shared key for communication is defined as K = gr_Ax_B + gr_Bx_A mod p.
a) Show the key derivation formulas of User A and User B (i.e., how does each
user compute the shared key?)
c) Does the protocol provide Forward Secrecy? Justify your answer.
Hire a Professional Essay & Assignment Writer for completing your Academic Assessments
2. Two questions related to the A1. For each question, you should use one sentence to highly summarize the problem (1 mark) and then use 1-3 sentences to explain it.
a)Briefly describe the issue when the adversary is able to know the secret key sk_s.
b)Briefly describe the problem when Alice’s algorithm always uses the same r for secure communications. (2 marks)
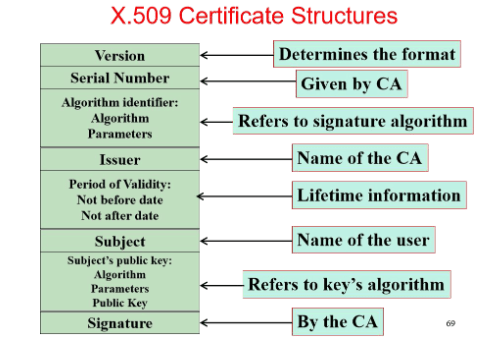
The CA generates the signature but the message to be signed excludes “Refer to Key’s Algorithm”. Describe how the adversary can launch the MITM attack on TLS protocol in the real world. You should start with the application scenario that user Alice wants to access the web resources manager by the web server Bob. You should use at least three steps to highly describe this kind of attack.
Buy Custom Answer of This Assessment & Raise Your Grades
Need Singapore assignment help review or assistance with CSCI368 Network Security Assignment? Look no further. Our Dissertation Writing Services cater to Singaporean students seeking expert guidance. From comprehensive reviews to tailored assignments, our experts ensure top-notch support for your academic success.
- Final Assignment: Migrating FashionOnline’s Infrastructure to AWS: A Strategy for Enhanced Availability and Data Protection
- HRM331: Talent Management – Strategic Shift from the War for Talent to the Wealth of Talent
- Marginalised Populations – The Structural and Cultural Exclusion of People Experiencing Homelessness in Singapore
- CVEN3501 Assignment 2: Groundwater Modelling of Drawdown from a Pumping Bore
- CSCI312 Assignment 2: Conceptual Modelling and Implementation of a Data Warehouse and Hive Queries
- CH2123 Assignment: Fugacity, VLE Modeling & Applications of Henry’s Law
- BAFI1045 Assignment -Constructing and Evaluating Passive and Active Portfolios Based on the Straits Times Index (STI)
- FIN2210E/FIN2212E Group Assignment: Financial Risk Management Analysis of Bursa Malaysia Companies
- FLM101 Assignment: A Film Analysis: Stylistic Techniques and Their Thematic Importance
- HRM Assignment Answer: Talent Transformation in the Age of AI: Turning Challenges into Opportunities via Ecosystem Innovation
UP TO 15 % DISCOUNT

